STP è definito nel 802.1d e identifica i percorsi più brevi in una rete con switch per realizzare una topologia ad albero priva di loop. L'albero logico comincia del bridge principale (root bridge) che viene identificato dal BID (Bridge ID) inviato con il frame BPDU.
In this example, there is a hierarchical network with access, distribution, and core layers. Each access layer switch is connected to two different distribution layer switches. Also, each distribution layer switch is connected to both core layer switches. By having multiple paths to get between PC1 and PC4, there is redundancy that can accommodate a single point of failure between the access and distribution layer, and between the distribution and core layer.
STP is enabled on all switches. For now, notice that STP has placed some switch ports in forwarding state and other switch ports in blocking state. This is to prevent loops in the Layer 2 network. STP will only use a redundant link if there is a failure on the primary link.
Layer 2 Loops
Redundancy is an important part of the hierarchical design. Although it is important for availability, there are some considerations that need to be addressed before redundancy is even possible on a network.
When multiple paths exist between two devices on the network and STP has been disabled on those switches, a Layer 2 loop can occur. If STP is enabled on these switches, which is the default, a Layer 2 loop would not occur.
Ethernet frames do not have a time to live (TTL) like IP packets traversing routers. As a result, if they are not terminated properly on a switched network, they continue to bounce from switch to switch endlessly or until a link is disrupted and breaks the loop.
Broadcast frames are forwarded out all switch ports, except the originating port. This ensures that all devices in the broadcast domain are able to receive the frame. If there is more than one path for the frame to be forwarded out, it can result in an endless loop.
Broadcast Storms
A broadcast storm occurs when there are so many broadcast frames caught in a Layer 2 loop that all available bandwidth is consumed. Consequently, no bandwidth is available bandwidth for legitimate traffic, and the network becomes unavailable for data communication.
A broadcast storm is inevitable on a looped network. As more devices send broadcasts out on the network, more and more traffic gets caught in the loop, eventually creating a broadcast storm that causes the network to fail.
There are other consequences for broadcast storms. Because broadcast traffic is forwarded out every port on a switch, all connected devices have to process all broadcast traffic that is being flooded endlessly around the looped network. This can cause the end device to malfunction because of the high processing requirements for sustaining such a high traffic load on the network interface card.
Duplicate Unicast Frames
Broadcast frames are not the only type of frames that are affected by loops. Unicast frames sent onto a looped network can result in duplicate frames arriving at the destination device.
Loops in the Wiring Closet
It happens when an administrator mistakenly connects a cable to the same switch it is already connected to. This usually occurs when network cables are not labeled or mislabeled or when the administrator has not taken the time to verify where the cables are connected.
There is an exception to this problem. An EtherChannel is a grouping of Ethernet ports on a switch that act as a single logical network connection. Because the switch treats the ports configured for the EtherChannel as a single network link, loops are not possible
Loops in the Cubicles
Because of insufficient network data connections, some end users have a personal hub or switch located in their working environment. Unlike the wiring closet, the administrator is not in control of how personal hubs and switches are being used or connected, so the end user can accidentally interconnect the switches or hubs.
In the example, the two user hubs are interconnected resulting in a network loop. The loop disrupts communication between all devices connected to switch S1.
The Spanning Tree Algorithm
Redundancy increases the availability of the network topology by protecting the network from a single point of failure, such as a failed network cable or switch. When redundancy is introduced into a Layer 2 design, loops and duplicate frames can occur.
STP ensures that there is only one logical path between all destinations on the network by intentionally blocking redundant paths that could cause a loop. A port is considered blocked when network traffic is prevented from entering or leaving that port. This does not include bridge protocol data unit (BPDU) frames that are used by STP to prevent loops. Blocking the redundant paths is critical to preventing loops on the network. The physical paths still exist to provide redundancy, but these paths are disabled to prevent the loops from occurring. If the path is ever needed to compensate for a network cable or switch failure, STP recalculates the paths and unblocks the necessary ports to allow the redundant path to become active.
STP uses the Spanning Tree Algorithm (STA) to determine which switch ports on a network need to be configured for blocking to prevent loops from occurring. The STA designates a single switch as the root bridge and uses it as the reference point for all path calculations. In the figure the root bridge, switch S1, is chosen through an election process. All switches participating in STP exchange BPDU frames to determine which switch has the lowest bridge ID (BID) on the network. The switch with the lowest BID automatically becomes the root bridge for the STA calculations.
The BPDU is the message frame exchanged by switches for STP. Each BPDU contains a BID that identifies the switch that sent the BPDU. The BID contains a priority value, the MAC address of the sending switch, and an optional extended system ID. The lowest BID value is determined by the combination of these three fields.
After the root bridge has been determined, the STA calculates the shortest path to the root bridge. Each switch uses the STA to determine which ports to block. While the STA determines the best paths to the root bridge for all destinations in the broadcast domain, all traffic is prevented from forwarding through the network. The STA considers both path and port costs when determining which path to leave unblocked. The path costs are calculated using port cost values associated with port speeds for each switch port along a given path. The sum of the port cost values determines the overall path cost to the root bridge. If there is more than one path to choose from, STA chooses the path with the lowest path cost.
When the STA has determined which paths are to be left available, it configures the switch ports into distinct port roles. The port roles describe their relation in the network to the root bridge and whether they are allowed to forward traffic.
Root ports - Switch ports closest to the root bridge. In the example, the root port on switch S2 is F0/1 configured for the trunk link between switch S2 and switch S1. The root port on switch S3 is F0/1, configured for the trunk link between switch S3 and switch S1.
Designated ports - All non-root ports that are still permitted to forward traffic on the network. In the example, switch ports F0/1 and F0/2 on switch S1 are designated ports. Switch S2 also has its port F0/2 configured as a designated port.
Non-designated ports - All ports configured to be in a blocking state to prevent loops. In the example, the STA configured port F0/2 on switch S3 in the non-designated role. Port F0/2 on switch S3 is in the blocking state.
The Root Bridge
Every spanning-tree instance (switched LAN or broadcast domain) has a switch designated as the root bridge. The root bridge serves as a reference point for all spanning-tree calculations to determine which redundant paths to block.
An election process determines which switch becomes the root bridge. All switches in the broadcast domain participate in the election process. After a switch boots, it sends out BPDU frames containing the switch BID and the root ID every 2 seconds. By default, the root ID matches the local BID for all switches on the network. The root ID identifies the root bridge on the network. Initially, each switch identifies itself as the root bridge after bootup.
As the switches forward their BPDU frames, adjacent switches in the broadcast domain read the root ID information from the BPDU frame. If the root ID from the BPDU received is lower than the root ID on the receiving switch, the receiving switch updates its root ID identifying the adjacent switch as the root bridge. Note: It may not be an adjacent switch, but any other switch in the broadcast domain. The switch then forwards new BPDU frames with the lower root ID to the other adjacent switches. Eventually, the switch with the lowest BID ends up being identified as the root bridge for the spanning-tree instance.
Best Paths to the Root Bridge
When the root bridge has been designated for the spanning-tree instance, the STA starts the process of determining the best paths to the root bridge from all destinations in the broadcast domain. The path information is determined by summing up the individual port costs along the path from the destination to the root bridge.
The default port costs are defined by the speed at which the port operates:
To configure the port cost of an interface, enter the spanning-tree cost value command in interface configuration mode. The range value can be between 1 and 200,000,000. To revert the port cost back to the default value, enter the no spanning-tree cost interface configuration command.
Path cost is the sum of all the port costs along the path to the root bridge. The paths with the lowest path cost become the preferred path, and all other redundant paths are blocked. In the example, the path cost from switch S2 to the root bridge switch S1, over path 1 is 19, while the path cost over path 2 is 38. Because path 1 has a lower overall path cost to the root bridge, it is the preferred path. STP then configures the redundant path to be blocked, preventing a loop from occurring.
To verify the port and path cost to the root bridge, enter the show spanning-tree privileged EXEC mode command. The Cost field in the output is the total path cost to the root bridge. This value changes depending on how many switch ports need to be traversed to get to the root bridge.
The BPDU Process
STP determines a root bridge for the spanning-tree instance by exchanging BPDUs. The BPDU frame contains 12 distinct fields that are used to convey path and priority information that STP uses to determine the root bridge and paths to the root bridge.
Each switch in the broadcast domain initially assumes that it is the root bridge for the spanning-tree instance, so the BPDU frames sent contain the BID of the local switch as the root ID. By default, BPDU frames are sent every 2 seconds after a switch is booted; that is, the default value of the hello timer specified in the BPDU frame is 2 seconds. Each switch maintains local information about its own BID, the root ID, and the path cost to the root.
When adjacent switches receive a BPDU frame, they compare the root ID from the BPDU frame with the local root ID. If the root ID in the BPDU is lower than the local root ID, the switch updates the local root ID and the ID in its BPDU messages. These messages serve to indicate the new root bridge on the network. Also, the path cost is updated to indicate how far away the root bridge is. For example, if the BPDU was received on a Fast Ethernet switch port, the path cost would be set to 19. If the local root ID is lower than the root ID received in the BPDU frame, the BPDU frame is discarded.
After a root ID has been updated to identify a new root bridge, all subsequent BPDU frames sent from that switch contain the new root ID and updated path cost. That way, all other adjacent switches are able to see the lowest root ID identified at all times. As the BPDU frames pass between other adjacent switches, the path cost is continually updated to indicate the total path cost to the root bridge. Each switch in the spanning tree uses its path costs to identify the best possible path to the root bridge.
Note: Priority is the initial deciding factor when choosing a root bridge. If the priority of all the switches was the same, the MAC address would be the deciding factor.
BID Fields
The bridge ID (BID) is used to determine the root bridge on a network. The BID field of a BPDU frame contains three separate fields: bridge priority, extended system ID, and MAC address. Each field is used during the root bridge election.
Bridge Priority
The bridge priority is a customizable value that you can use to influence which switch becomes the root bridge. The switch with the lowest priority, which means lowest BID, becomes the root bridge (the lower the priority value, the higher the priority). For example, to ensure that a specific switch is always the root bridge, you set the priority to a lower value than the rest of the switches on the network. The default value for the priority of all Cisco switches is 32768. The priority range is between 1 and 65536; therefore, 1 is the highest priority
Extended System ID
As shown in the example, the extended system ID can be omitted in BPDU frames in certain configurations. The early implementation of STP was designed for networks that did not use VLANs. There was a single common spanning tree across all switches. When VLANs started to become common for network infrastructure segmentation, STP was enhanced to include support for VLANs. As a result, the extended system ID field contains the ID of the VLAN with which the BPDU is associated.
When the extended system ID is used, it changes the number of bits available for the bridge priority value, so the increment for the bridge priority value changes from 1 to 4096. Therefore, bridge priority values can only be multiples of 4096.
The extended system ID value is added to the bridge priority value in the BID to identify the priority and VLAN of the BPDU frame.
MAC Address
When two switches are configured with the same priority and have the same extended system ID, the switch with the MAC address with the lowest hexadecimal value has the lower BID. Initially, all switches are configured with the same default priority value. The MAC address is then the deciding factor on which switch is going to become the root bridge. This results in an unpredictable choice for the root bridge. It is recommended to configure the desired root bridge switch with a lower priority to ensure that it is elected root bridge. This also ensures that the addition of new switches to the network does not trigger a new spanning-tree election, which could disrupt network communication while a new root bridge is being selected.
Configure and Verify the BID
When a specific switch is to become a root bridge, the bridge priority value needs to be adjusted to ensure it is lower than the bridge priority values of all the other switches on the network. There are two different configuration methods that you can use to configure the bridge priority value on a Cisco Catalyst switch.
Method 1 - To ensure that the switch has the lowest bridge priority value, use the spanning-tree vlan vlan-id root primary command in global configuration mode. The priority for the switch is set to the predefined value of 24576 or to the next 4096 decrement value below the lowest bridge priority detected on the network.
If an alternate root bridge is desired, use the spanning-tree vlan vlan-id root secondary global configuration mode command. This command sets the priority for the switch to the predefined value of 28672. This ensures that this switch becomes the root bridge if the primary root bridge fails and a new root bridge election occurs and assuming that the rest of the switches in the network have the default 32768 priority value defined.
In the example, switch S1 has been assigned as the primary root bridge using the spanning-tree vlan 1 root primary global configuration mode command, and switch S2 has been configured as the secondary root bridge using the spanning-tree vlan 1 root secondary global configuration mode command.
Method 2 - Another method for configuring the bridge priority value is using the spanning-tree vlan vlan-id priority value global configuration mode command. This command gives you more granular control over the bridge priority value. The priority value is configured in increments of 4096 between 0 and 65536.
Port Roles
The root bridge is elected for the spanning-tree instance. The location of the root bridge in the network topology determines how port roles are calculated.
There are four distinct port roles that switch ports are automatically configured for during the spanning-tree process.
1. Root Port
The root port exists on non-root bridges and is the switch port with the best path to the root bridge. Root ports forward traffic toward the root bridge. The source MAC address of frames received on the root port are capable of populating the MAC table. Only one root port is allowed per bridge.
2. Designated Port
The designated port exists on root and non-root bridges. For root bridges, all switch ports are designated ports. For non-root bridges, a designated port is the switch port that receives and forwards frames toward the root bridge as needed. Only one designated port is allowed per segment. If multiple switches exist on the same segment, an election process determines the designated switch, and the corresponding switch port begins forwarding frames for the segment. Designated ports are capable of populating the MAC table.
3. Non-designated Port
The non-designated port is a switch port that is blocked, so it is not forwarding data frames and not populating the MAC address table with source addresses. A non-designated port is not a root port or a designated port. For some variants of STP, the non-designated port is called an alternate port.
4. Disabled Port
The disabled port is a switch port that is administratively shut down. A disabled port does not function in the spanning-tree process.
The STA determines which port role is assigned to each switch port.
When determining the root port on a switch, the switch compares the path costs on all switch ports participating in the spanning tree. The switch port with the lowest overall path cost to the root is automatically assigned the root port role because it is closest to the root bridge. In a network topology below, all switches that are using spanning tree, except for the root bridge, have a single root port defined.
When there are two switch ports that have the same path cost to the root bridge and both are the lowest path costs on the switch, the switch needs to determine which switch port is the root port. The switch uses the customizable port priority value, or the lowest port ID if both port priority values are the same.
The port ID is the interface ID of the switch port. For example, the figure shows four switches. Port F0/1 and F0/2 on switch S2 have the same path cost value back to the root bridge. However, port F0/1 on switch S2 is the preferred port because it has a lower port ID value.
The port ID is appended to the port priority. For example, switch port F0/1 has a default port priority value of 128.1, where 128 is the configurable port priority value, and .1 is the port ID. Switch port F0/2 has a port priority value of 128.2, by default.
Configure Port Priority
You can configure the port priority value using the spanning-tree port-priority value interface configuration mode command. The port priority values range from 0 - 240, in increments of 16. The default port priority value is 128. As with bridge priority, lower port priority values give the port higher priority.
In the example, the port priority for port F0/1 has been set to 112, which is below the default port priority of 128. This ensures that the port is the preferred port when competing with another port for a specific port role.
When the switch decides to use one port over another for the root port, the other is configured as a non-designated port to prevent a loop from occurring.
Port Role Decisions
In the example, switch S1 is the root bridge. Switches S2 and S3 have root ports configured for the ports connecting back to S1.
After a switch has determined which of its ports is configured in the root port role, it needs to decide which ports have the designated and non-designated roles.
The root bridge automatically configures all of its switch ports in the designated role. Other switches in the topology configure their non-root ports as designated or non-designated ports.
Designated ports are configured for all LAN segments. When two switches are connected to the same LAN segment, and root ports have already been defined, the two switches have to decide which port gets to be configured as a designated port and which one is left as the non-designated port.
The switches on the LAN segment in question exchange BPDU frames, which contain the switch BID. Generally, the switch with the lower BID has its port configured as a designated port, while the switch with the higher BID has its port configured as a non-designated port. However, keep in mind that the first priority is the lowest path cost to the root bridge and that only if the port costs are equal, is the BID of the sender used.
As a result, each switch determines which port roles are assigned to each of its ports to create the loop-free spanning tree.
BPDU Timers
The amount of time that a port stays in the various port states depends on the BPDU timers. Only the switch in the role of root bridge may send information through the tree to adjust the timers. The following timers determine STP performance and state changes:
Cisco PortFast Technology
PortFast is a Cisco technology. When a switch port configured with PortFast is configured as an access port, that port transitions from blocking to forwarding state immediately, bypassing the typical STP listening and learning states. You can use PortFast on access ports, which are connected to a single workstation or to a server, to allow those devices to connect to the network immediately rather than waiting for spanning tree to converge. If an interface configured with PortFast receives a BPDU frame, spanning tree can put the port into the blocking state using a feature called BPDU guard.
Note: Cisco PortFast technology can be used to support DHCP. Without PortFast, a PC can send a DHCP request before the port is in forwarding state, denying the host from getting a usable IP address and other information. Because PortFast immediately changes the state to forwarding, the PC always gets a usable IP address.
Note: Because the purpose of PortFast is to minimize the time that access ports must wait for spanning tree to converge, it should be used only on access ports. If you enable PortFast on a port connecting to another switch, you risk creating a spanning-tree loop.
To configure PortFast on a switch port, enter the spanning-tree portfast interface configuration mode command on each interface that PortFast is to be enabled.
To disable PortFast, enter the no spanning-tree portfast interface configuration mode command on each interface that PortFast is to be disabled.
To verify that PortFast has been enabled for a switch port, use the show running-config privileged EXEC mode command. The absence of the spanning-tree portfast command in the running configuration for an interface indicates that PortFast has been disabled for that interface. PortFast is disabled on all interfaces by default.
STP Convergence
Convergence is an important aspect of the spanning-tree process. Convergence is the time it takes for the network to determine which switch is going to assume the role of the root bridge, go through all the different port states, and set all switch ports to their final spanning-tree port roles where all potential loops are eliminated. The convergence process takes time to complete because of the different timers used to coordinate the process.
To understand the convergence process more thoroughly, it has been broken down into three distinct steps:
Step 1. Elect a root bridge
Step 2. Elect root ports
Step 3. Elect designated and non-designated ports
Step 1. Electing a Root Bridge
The first step of the spanning-tree convergence process is to elect a root bridge. The root bridge is the basis for all spanning-tree path cost calculations and ultimately leads to the assignment of the different port roles used to prevent loops from occurring.
A root bridge election is triggered after a switch has finished booting up, or when a path failure has been detected on a network. Initially, all switch ports are configured for the blocking state, which by default lasts 20 seconds. This is done to prevent a loop from occurring before STP has had time to calculate the best root paths and configure all switch ports to their specific roles. While the switch ports are in a blocking state, they are still able to send and receive BPDU frames so that the spanning-tree root election can proceed. Spanning tree supports a maximum network diameter of seven switch hops from end to end. This allows the entire root bridge election process to occur within 14 seconds, which is less than the time the switch ports spend in the blocking state.
Immediately after the switches have finished booting up, they start sending BPDU frames advertising their BID in an attempt to become the root bridge. Initially, all switches in the network assume that they are the root bridge for the broadcast domain. The flood of BPDU frames on the network have the root ID field matching the BID field, indicating that each switch considers itself the root bridge. These BPDU frames are sent every 2 seconds based on the default hello timer value.
As each switch receives the BPDU frames from its neighboring switches, they compare the root ID from the received BPDU frame with the root ID configured locally. If the root ID from the received BPDU frame is lower than the root ID it currently has, the root ID field is updated indicating the new best candidate for the root bridge role.
After the root ID field is updated on a switch, the switch then incorporates the new root ID in all future BPDU frame transmissions. This ensures that the lowest root ID is always conveyed to all other adjacent switches in the network. The root bridge election ends once the lowest bridge ID populates the root ID field of all switches in the broadcast domain.
Even though the root bridge election process has completed, the switches continue to forward their BPDU frames advertising the root ID of the root bridge every 2 seconds. Each switch is configured with a max age timer that determines how long a switch retains the current BPDU configuration in the event it stops receiving updates from its neighboring switches. By default, the max age timer is set to 20 seconds. Therefore, if a switch fails to receive 10 consecutive BPDU frames from one of its neighbors, the switch assumes that a logical path in the spanning tree has failed and that the BPDU information is no longer valid. This triggers another spanning-tree root bridge election.
When the root bridge election is completed, you can verify the identity of the root bridge using the show spanning-tree privileged EXEC mode command
In the topology example, switch S1 has the lowest priority value of the three switches, so we can assume it will become the root bridge.
Step 2. Elect Root Ports
Now that the root bridge has been determined, the switches start configuring the port roles for each of their switch ports. The first port role that needs to be determined is the root port role.
Every switch in a spanning-tree topology, except for the root bridge, has a single root port defined. The root port is the switch port with the lowest path cost to the root bridge. Normally path cost alone determines which switch port becomes the root port. However, additional port characteristics determine the root port when two or more ports on the same switch have the same path cost to the root. This can happen when redundant links are used to uplink one switch to another switch when an EtherChannel configuration is not used.
Switch ports with equivalent path costs to the root use the configurable port priority value. They use the port ID to break a tie. When a switch chooses one equal path cost port as a root port over another, the losing port is configured as the non-designated to avoid a loop.
The process of determining which port becomes a root port happens during the root bridge election BPDU exchange. Path costs are updated immediately when BPDU frames arrive indicating a new root ID or redundant path. At the time the path cost is updated, the switch enters decision mode to determine if port configurations need to be updated. The port role decisions do not wait until all switches settle on which switch is going to be the final root bridge. As a result, the port role for a given switch port may change multiple times during convergence, until it finally settles on its final port role after the root ID changes for the last time.
Rapid per-VLAN spanning tree protocol (rapid PVST+) - Based on the IEEE 802.1w standard and has a faster convergence than STP (standard 802.1D). Rapid PVST+ includes Cisco-proprietary extensions such as BackboneFast, UplinkFast, and PortFast.
Rapid spanning tree protocol (RSTP) - It provides faster spanning-tree convergence after a topology change. RSTP implements the Cisco-proprietary STP extensions, BackboneFast, UplinkFast, and PortFast, into the public standard.
Multiple STP (MSTP) - Enables multiple VLANs to be mapped to the same spanning-tree instance, reducing the number of instances needed to support a large number of VLANs. MSTP was inspired by the Cisco-proprietary Multiple Instances STP (MISTP) and is an evolution of STP and RSTP. MSTP provides for multiple forwarding paths for data traffic and enables load balancing.
PVST+
Cisco developed PVST+ so that a network can run an STP instance for each VLAN in the network. With PVST+, more than one trunk can block for a VLAN and load sharing can be implemented. However, implementing PVST+ means that all switches in the network are engaged in converging the network, and the switch ports have to accommodate the additional bandwidth used for each PVST+ instance to send its own BPDUs.
In a Cisco PVST+ environment, you can tune the spanning-tree parameters so that half of the VLANs forward on each uplink trunk. In the figure, port F0/3 on switch S2 is the forwarding port for VLAN 20, and F0/2 on switch S2 is the forwarding port for VLAN 10. This is accomplished by configuring one switch to be elected the root bridge for half of the total number of VLANs in the network, and a second switch to be elected the root bridge for the other half of the VLANs. In the figure, switch S3 is the root bridge for VLAN 20, and switch S1 is the root bridge for VLAN 10. Creating different STP root switches per VLAN creates a more redundant network.
PVST+ Bridge ID
As you recall, in the original 802.1D standard, an 8-byte BID is composed of a 2-byte bridge priority and a 6-byte MAC address of the switch. There was no need to identify a VLAN because there was only one spanning tree in a network. PVST+ requires that a separate instance of spanning tree run for each VLAN. To support PVST+, the 8-byte BID field is modified to carry a VLAN ID (VID).
The following provides more details on the PVST+ fields:
The MAC address is what makes a BID unique. When the priority and extended system ID are prepended to the switch MAC address, each VLAN on the switch can be represented by a unique BID.
Caution: If no priority has been configured, every switch has the same default priority, and the election of the root bridge for each VLAN is based on the MAC address. Therefore, to ensure that you get the root bridge you want, it is advisable to assign a lower priority value to the switch that should serve as the root bridge.
Configure PVST+
The topology shows three switches with 802.1Q trunks connecting them. There are two VLANs, 10 and 20, which are being trunked across these links. This network has not been configured for spanning tree. The goal is to configure S3 as the root bridge for VLAN 20 and S1 as the root bridge for VLAN 10. Port F0/3 on S2 is the forwarding port for VLAN 20 and the blocking port for VLAN 10. Port F0/2 on S2 is the forwarding port for VLAN 10 and the blocking port for VLAN 20.
Configure the Primary Root Bridges
The goal is to configure switch S3 as the primary root bridge for VLAN 20 and configure switch S1 as the primary root bridge for VLAN 10. To configure a switch to become the root bridge for a specified VLAN, use the spanning-tree vlan vlan-ID root primary global configuration mode command.
Configure the Secondary Root Bridges
A secondary root is a switch that may become the root bridge for a VLAN if the primary root bridge fails. To configure a switch as the secondary root bridge, use the spanning-tree vlan vlan-ID root secondary global configuration mode command. Assuming the other bridges in the VLAN retain their default STP priority, this switch becomes the root bridge if the primary root bridge fails. This command can be executed on more than one switch to configure multiple backup root bridges.
PVST+ Switch Priority
You can set the switch priority for the specified spanning-tree instance. This setting affects the likelihood that this switch is selected as the root switch. A lower value increases the probability that the switch is selected. The range is 0 to 61440 in increments of 4096. For example, a valid priority value is 4096x2 = 8192. All other values are rejected.
RSTP can achieve much faster convergence in a properly configured network, sometimes in as little as a few hundred milliseconds. RSTP redefines the type of ports and their state. If a port is configured to be an alternate or a backup port it can immediately change to a forwarding state without waiting for the network to converge
RSTP BPDU
RSTP (802.1w) uses type 2, version 2 BPDUs, so an RSTP bridge can communicate 802.1D on any shared link or with any switch running 802.1D. RSTP sends BPDUs and populates the flag byte in a slightly different manner than in 802.1D:
Il Rapid STP (802.1w) ha la stessa funzione di 802.1d ma lo fa più velocemente. La migliore velocità è ottenuta dal fatto che le porte possono passare subito da blocking (discarding) a forwarding.
Note: Like STP, an RSTP bridge sends a BPDU with its current information every hello time period (2 seconds by default), even if the RSTP bridge does not receive any BPDUs from the root bridge.
Edge Ports
An RSTP edge port is a switch port that is never intended to be connected to another switch device. It immediately transitions to the forwarding state when enabled.
The edge port concept is well known to Cisco spanning-tree users, because it corresponds to the PortFast feature in which all ports directly connected to end stations anticipate that no switch device is connected to them. The PortFast ports immediately transition to the STP forwarding state, thereby skipping the time-consuming listening and learning stages. Neither edge ports nor PortFast-enabled ports generate topology changes when the port transitions to a disabled or enabled status.
Unlike PortFast, an RSTP edge port that receives a BPDU loses its edge port status immediately and becomes a normal spanning-tree port.
The Cisco RSTP implementation maintains the PortFast keyword using the spanning-tree portfast command for edge port configuration. Configuring an edge port to be attached to another switch can have negative implications for RSTP when it is in sync state because a temporary loop can result, possibly delaying the convergence of RSTP due to BPDU contention with loop traffic.
RSTP Port States
RSTP provides rapid convergence following a failure or during re-establishment of a switch, switch port, or link. An RSTP topology change causes a transition in the appropriate switch ports to the forwarding state through either explicit handshakes or a proposal and agreement process and synchronization.
With RSTP, the role of a port is separated from the state of a port. For example, a designated port could be in the discarding state temporarily, even though its final state is to be forwarding. The figure shows the three possible RSTP port states: discarding, learning, and forwarding.
In IEEE 802.1D STP, when a port has been selected by spanning tree to become a designated port, it must wait two times the forward delay before transitioning the port to the forwarding state. RSTP significantly speeds up the recalculation process after a topology change, because it converges on a link-by-link basis and does not rely on timers expiring before ports can transition. Rapid transition to the forwarding state can only be achieved on edge ports and point-to-point links. In RSTP, this condition corresponds to a designated port in the discarding state.
Configuring Rapid-PVST+
The figure shows the Cisco IOS command syntax needed to configure rapid-PVST+ on a Cisco switch:
Note: If you connect a port configured with the spanning-tree link-type point-to-point command to a remote port through a point-to-point link and the local port becomes a designated port, the switch negotiates with the remote port and rapidly changes the local port to the forwarding state.
Note: When a port is configured with the clear spanning-tree detected-protocols command and that port is connected to a port on a legacy IEEE 802.1D switch, the Cisco IOS software restarts the protocol migration process on the entire switch
Troubleshoot STP Operation
An issue that is not well known relates to the diameter of the switched network. The conservative default values for the STP timers impose a maximum network diameter of seven. In the figure this design creates a network diameter of eight. The maximum network diameter restricts how far away swtiches in the network can be from each other. In this case, two distinct switches cannot be more than seven hops away. Part of this restriction comes from the age field that BPDUs carry.
When a BPDU propagates from the root bridge toward the leaves of the tree, the age field increments each time the BPDU goes though a switch. Eventually, the switch discards the BPDU when the age field goes beyond maximum age. If the root is too far away from some switches of the network, BPDUs will be dropped. This issue affects convergence of the spanning tree.
Take special care if you plan to change STP timers from the default value. There is danger if you try to get faster convergence in this way. An STP timer change has an impact on the diameter of the network and the stability of the STP. You can change the switch priority to select the root bridge, and change the port cost or priority parameter to control redundancy and load balancing.
Because of insufficient network data connections, some end users have a personal hub or switch located in their working environment. Unlike the wiring closet, the administrator is not in control of how personal hubs and switches are being used or connected, so the end user can accidentally interconnect the switches or hubs.
In the example, the two user hubs are interconnected resulting in a network loop. The loop disrupts communication between all devices connected to switch S1.
The Spanning Tree Algorithm
Redundancy increases the availability of the network topology by protecting the network from a single point of failure, such as a failed network cable or switch. When redundancy is introduced into a Layer 2 design, loops and duplicate frames can occur.
STP ensures that there is only one logical path between all destinations on the network by intentionally blocking redundant paths that could cause a loop. A port is considered blocked when network traffic is prevented from entering or leaving that port. This does not include bridge protocol data unit (BPDU) frames that are used by STP to prevent loops. Blocking the redundant paths is critical to preventing loops on the network. The physical paths still exist to provide redundancy, but these paths are disabled to prevent the loops from occurring. If the path is ever needed to compensate for a network cable or switch failure, STP recalculates the paths and unblocks the necessary ports to allow the redundant path to become active.
STP uses the Spanning Tree Algorithm (STA) to determine which switch ports on a network need to be configured for blocking to prevent loops from occurring. The STA designates a single switch as the root bridge and uses it as the reference point for all path calculations. In the figure the root bridge, switch S1, is chosen through an election process. All switches participating in STP exchange BPDU frames to determine which switch has the lowest bridge ID (BID) on the network. The switch with the lowest BID automatically becomes the root bridge for the STA calculations.
The BPDU is the message frame exchanged by switches for STP. Each BPDU contains a BID that identifies the switch that sent the BPDU. The BID contains a priority value, the MAC address of the sending switch, and an optional extended system ID. The lowest BID value is determined by the combination of these three fields.
After the root bridge has been determined, the STA calculates the shortest path to the root bridge. Each switch uses the STA to determine which ports to block. While the STA determines the best paths to the root bridge for all destinations in the broadcast domain, all traffic is prevented from forwarding through the network. The STA considers both path and port costs when determining which path to leave unblocked. The path costs are calculated using port cost values associated with port speeds for each switch port along a given path. The sum of the port cost values determines the overall path cost to the root bridge. If there is more than one path to choose from, STA chooses the path with the lowest path cost.
When the STA has determined which paths are to be left available, it configures the switch ports into distinct port roles. The port roles describe their relation in the network to the root bridge and whether they are allowed to forward traffic.
Root ports - Switch ports closest to the root bridge. In the example, the root port on switch S2 is F0/1 configured for the trunk link between switch S2 and switch S1. The root port on switch S3 is F0/1, configured for the trunk link between switch S3 and switch S1.
Designated ports - All non-root ports that are still permitted to forward traffic on the network. In the example, switch ports F0/1 and F0/2 on switch S1 are designated ports. Switch S2 also has its port F0/2 configured as a designated port.
Non-designated ports - All ports configured to be in a blocking state to prevent loops. In the example, the STA configured port F0/2 on switch S3 in the non-designated role. Port F0/2 on switch S3 is in the blocking state.
The Root Bridge
Every spanning-tree instance (switched LAN or broadcast domain) has a switch designated as the root bridge. The root bridge serves as a reference point for all spanning-tree calculations to determine which redundant paths to block.
An election process determines which switch becomes the root bridge. All switches in the broadcast domain participate in the election process. After a switch boots, it sends out BPDU frames containing the switch BID and the root ID every 2 seconds. By default, the root ID matches the local BID for all switches on the network. The root ID identifies the root bridge on the network. Initially, each switch identifies itself as the root bridge after bootup.
As the switches forward their BPDU frames, adjacent switches in the broadcast domain read the root ID information from the BPDU frame. If the root ID from the BPDU received is lower than the root ID on the receiving switch, the receiving switch updates its root ID identifying the adjacent switch as the root bridge. Note: It may not be an adjacent switch, but any other switch in the broadcast domain. The switch then forwards new BPDU frames with the lower root ID to the other adjacent switches. Eventually, the switch with the lowest BID ends up being identified as the root bridge for the spanning-tree instance.
Best Paths to the Root Bridge
When the root bridge has been designated for the spanning-tree instance, the STA starts the process of determining the best paths to the root bridge from all destinations in the broadcast domain. The path information is determined by summing up the individual port costs along the path from the destination to the root bridge.
The default port costs are defined by the speed at which the port operates:
To configure the port cost of an interface, enter the spanning-tree cost value command in interface configuration mode. The range value can be between 1 and 200,000,000. To revert the port cost back to the default value, enter the no spanning-tree cost interface configuration command.
Path cost is the sum of all the port costs along the path to the root bridge. The paths with the lowest path cost become the preferred path, and all other redundant paths are blocked. In the example, the path cost from switch S2 to the root bridge switch S1, over path 1 is 19, while the path cost over path 2 is 38. Because path 1 has a lower overall path cost to the root bridge, it is the preferred path. STP then configures the redundant path to be blocked, preventing a loop from occurring.
To verify the port and path cost to the root bridge, enter the show spanning-tree privileged EXEC mode command. The Cost field in the output is the total path cost to the root bridge. This value changes depending on how many switch ports need to be traversed to get to the root bridge.
The BPDU Process
STP determines a root bridge for the spanning-tree instance by exchanging BPDUs. The BPDU frame contains 12 distinct fields that are used to convey path and priority information that STP uses to determine the root bridge and paths to the root bridge.
Each switch in the broadcast domain initially assumes that it is the root bridge for the spanning-tree instance, so the BPDU frames sent contain the BID of the local switch as the root ID. By default, BPDU frames are sent every 2 seconds after a switch is booted; that is, the default value of the hello timer specified in the BPDU frame is 2 seconds. Each switch maintains local information about its own BID, the root ID, and the path cost to the root.
When adjacent switches receive a BPDU frame, they compare the root ID from the BPDU frame with the local root ID. If the root ID in the BPDU is lower than the local root ID, the switch updates the local root ID and the ID in its BPDU messages. These messages serve to indicate the new root bridge on the network. Also, the path cost is updated to indicate how far away the root bridge is. For example, if the BPDU was received on a Fast Ethernet switch port, the path cost would be set to 19. If the local root ID is lower than the root ID received in the BPDU frame, the BPDU frame is discarded.
After a root ID has been updated to identify a new root bridge, all subsequent BPDU frames sent from that switch contain the new root ID and updated path cost. That way, all other adjacent switches are able to see the lowest root ID identified at all times. As the BPDU frames pass between other adjacent switches, the path cost is continually updated to indicate the total path cost to the root bridge. Each switch in the spanning tree uses its path costs to identify the best possible path to the root bridge.
Note: Priority is the initial deciding factor when choosing a root bridge. If the priority of all the switches was the same, the MAC address would be the deciding factor.
BID Fields
The bridge ID (BID) is used to determine the root bridge on a network. The BID field of a BPDU frame contains three separate fields: bridge priority, extended system ID, and MAC address. Each field is used during the root bridge election.
Bridge Priority
The bridge priority is a customizable value that you can use to influence which switch becomes the root bridge. The switch with the lowest priority, which means lowest BID, becomes the root bridge (the lower the priority value, the higher the priority). For example, to ensure that a specific switch is always the root bridge, you set the priority to a lower value than the rest of the switches on the network. The default value for the priority of all Cisco switches is 32768. The priority range is between 1 and 65536; therefore, 1 is the highest priority
Extended System ID
As shown in the example, the extended system ID can be omitted in BPDU frames in certain configurations. The early implementation of STP was designed for networks that did not use VLANs. There was a single common spanning tree across all switches. When VLANs started to become common for network infrastructure segmentation, STP was enhanced to include support for VLANs. As a result, the extended system ID field contains the ID of the VLAN with which the BPDU is associated.
When the extended system ID is used, it changes the number of bits available for the bridge priority value, so the increment for the bridge priority value changes from 1 to 4096. Therefore, bridge priority values can only be multiples of 4096.
The extended system ID value is added to the bridge priority value in the BID to identify the priority and VLAN of the BPDU frame.
MAC Address
When two switches are configured with the same priority and have the same extended system ID, the switch with the MAC address with the lowest hexadecimal value has the lower BID. Initially, all switches are configured with the same default priority value. The MAC address is then the deciding factor on which switch is going to become the root bridge. This results in an unpredictable choice for the root bridge. It is recommended to configure the desired root bridge switch with a lower priority to ensure that it is elected root bridge. This also ensures that the addition of new switches to the network does not trigger a new spanning-tree election, which could disrupt network communication while a new root bridge is being selected.
Configure and Verify the BID
When a specific switch is to become a root bridge, the bridge priority value needs to be adjusted to ensure it is lower than the bridge priority values of all the other switches on the network. There are two different configuration methods that you can use to configure the bridge priority value on a Cisco Catalyst switch.
Method 1 - To ensure that the switch has the lowest bridge priority value, use the spanning-tree vlan vlan-id root primary command in global configuration mode. The priority for the switch is set to the predefined value of 24576 or to the next 4096 decrement value below the lowest bridge priority detected on the network.
If an alternate root bridge is desired, use the spanning-tree vlan vlan-id root secondary global configuration mode command. This command sets the priority for the switch to the predefined value of 28672. This ensures that this switch becomes the root bridge if the primary root bridge fails and a new root bridge election occurs and assuming that the rest of the switches in the network have the default 32768 priority value defined.
In the example, switch S1 has been assigned as the primary root bridge using the spanning-tree vlan 1 root primary global configuration mode command, and switch S2 has been configured as the secondary root bridge using the spanning-tree vlan 1 root secondary global configuration mode command.
Method 2 - Another method for configuring the bridge priority value is using the spanning-tree vlan vlan-id priority value global configuration mode command. This command gives you more granular control over the bridge priority value. The priority value is configured in increments of 4096 between 0 and 65536.
Port Roles
The root bridge is elected for the spanning-tree instance. The location of the root bridge in the network topology determines how port roles are calculated.
There are four distinct port roles that switch ports are automatically configured for during the spanning-tree process.
1. Root Port
The root port exists on non-root bridges and is the switch port with the best path to the root bridge. Root ports forward traffic toward the root bridge. The source MAC address of frames received on the root port are capable of populating the MAC table. Only one root port is allowed per bridge.
2. Designated Port
The designated port exists on root and non-root bridges. For root bridges, all switch ports are designated ports. For non-root bridges, a designated port is the switch port that receives and forwards frames toward the root bridge as needed. Only one designated port is allowed per segment. If multiple switches exist on the same segment, an election process determines the designated switch, and the corresponding switch port begins forwarding frames for the segment. Designated ports are capable of populating the MAC table.
3. Non-designated Port
The non-designated port is a switch port that is blocked, so it is not forwarding data frames and not populating the MAC address table with source addresses. A non-designated port is not a root port or a designated port. For some variants of STP, the non-designated port is called an alternate port.
4. Disabled Port
The disabled port is a switch port that is administratively shut down. A disabled port does not function in the spanning-tree process.
The STA determines which port role is assigned to each switch port.
When determining the root port on a switch, the switch compares the path costs on all switch ports participating in the spanning tree. The switch port with the lowest overall path cost to the root is automatically assigned the root port role because it is closest to the root bridge. In a network topology below, all switches that are using spanning tree, except for the root bridge, have a single root port defined.
When there are two switch ports that have the same path cost to the root bridge and both are the lowest path costs on the switch, the switch needs to determine which switch port is the root port. The switch uses the customizable port priority value, or the lowest port ID if both port priority values are the same.
The port ID is the interface ID of the switch port. For example, the figure shows four switches. Port F0/1 and F0/2 on switch S2 have the same path cost value back to the root bridge. However, port F0/1 on switch S2 is the preferred port because it has a lower port ID value.
The port ID is appended to the port priority. For example, switch port F0/1 has a default port priority value of 128.1, where 128 is the configurable port priority value, and .1 is the port ID. Switch port F0/2 has a port priority value of 128.2, by default.
Configure Port Priority
You can configure the port priority value using the spanning-tree port-priority value interface configuration mode command. The port priority values range from 0 - 240, in increments of 16. The default port priority value is 128. As with bridge priority, lower port priority values give the port higher priority.
In the example, the port priority for port F0/1 has been set to 112, which is below the default port priority of 128. This ensures that the port is the preferred port when competing with another port for a specific port role.
When the switch decides to use one port over another for the root port, the other is configured as a non-designated port to prevent a loop from occurring.
Port Role Decisions
In the example, switch S1 is the root bridge. Switches S2 and S3 have root ports configured for the ports connecting back to S1.
After a switch has determined which of its ports is configured in the root port role, it needs to decide which ports have the designated and non-designated roles.
The root bridge automatically configures all of its switch ports in the designated role. Other switches in the topology configure their non-root ports as designated or non-designated ports.
Designated ports are configured for all LAN segments. When two switches are connected to the same LAN segment, and root ports have already been defined, the two switches have to decide which port gets to be configured as a designated port and which one is left as the non-designated port.
The switches on the LAN segment in question exchange BPDU frames, which contain the switch BID. Generally, the switch with the lower BID has its port configured as a designated port, while the switch with the higher BID has its port configured as a non-designated port. However, keep in mind that the first priority is the lowest path cost to the root bridge and that only if the port costs are equal, is the BID of the sender used.
As a result, each switch determines which port roles are assigned to each of its ports to create the loop-free spanning tree.
Verifying Port Roles and Port Priority
Now that spanning tree has determined the logical loop-free network topology, you may want to confirm which port roles and port priorities are configured for the various switch ports in the network.
To verify the port roles and port priorities for the switch ports, use the show spanning-tree privileged EXEC mode command.
Port States
STP determines the logical loop-free path throughout the broadcast domain. The spanning tree is determined through the information learned by the exchange of the BPDU frames between the interconnected switches. To facilitate the learning of the logical spanning tree, each switch port transitions through five possible port states and three BPDU timers:
- Blocking - The port is a non-designated port and does not participate in frame forwarding. The port receives BPDU frames to determine the location and root ID of the root bridge switch and what port roles each switch port should assume in the final active STP topology.
- Listening - STP has determined that the port can participate in frame forwarding according to the BPDU frames that the switch has received thus far. At this point, the switch port is not only receiving BPDU frames, it is also transmitting its own BPDU frames and informing adjacent switches that the switch port is preparing to participate in the active topology.
- Learning - The port prepares to participate in frame forwarding and begins to populate the MAC address table.
- Forwarding - The port is considered part of the active topology and forwards frames and also sends and receives BPDU frames.
- Disabled - The Layer 2 port does not participate in spanning tree and does not forward frames. The disabled state is set when the switch port is administratively disabled.
BPDU Timers
The amount of time that a port stays in the various port states depends on the BPDU timers. Only the switch in the role of root bridge may send information through the tree to adjust the timers. The following timers determine STP performance and state changes:
- Hello time
- Forward delay
- Maximum age
Cisco PortFast Technology
PortFast is a Cisco technology. When a switch port configured with PortFast is configured as an access port, that port transitions from blocking to forwarding state immediately, bypassing the typical STP listening and learning states. You can use PortFast on access ports, which are connected to a single workstation or to a server, to allow those devices to connect to the network immediately rather than waiting for spanning tree to converge. If an interface configured with PortFast receives a BPDU frame, spanning tree can put the port into the blocking state using a feature called BPDU guard.
Note: Cisco PortFast technology can be used to support DHCP. Without PortFast, a PC can send a DHCP request before the port is in forwarding state, denying the host from getting a usable IP address and other information. Because PortFast immediately changes the state to forwarding, the PC always gets a usable IP address.
Note: Because the purpose of PortFast is to minimize the time that access ports must wait for spanning tree to converge, it should be used only on access ports. If you enable PortFast on a port connecting to another switch, you risk creating a spanning-tree loop.
To configure PortFast on a switch port, enter the spanning-tree portfast interface configuration mode command on each interface that PortFast is to be enabled.
To disable PortFast, enter the no spanning-tree portfast interface configuration mode command on each interface that PortFast is to be disabled.
To verify that PortFast has been enabled for a switch port, use the show running-config privileged EXEC mode command. The absence of the spanning-tree portfast command in the running configuration for an interface indicates that PortFast has been disabled for that interface. PortFast is disabled on all interfaces by default.
Convergence is an important aspect of the spanning-tree process. Convergence is the time it takes for the network to determine which switch is going to assume the role of the root bridge, go through all the different port states, and set all switch ports to their final spanning-tree port roles where all potential loops are eliminated. The convergence process takes time to complete because of the different timers used to coordinate the process.
To understand the convergence process more thoroughly, it has been broken down into three distinct steps:
Step 1. Elect a root bridge
Step 2. Elect root ports
Step 3. Elect designated and non-designated ports
Step 1. Electing a Root Bridge
The first step of the spanning-tree convergence process is to elect a root bridge. The root bridge is the basis for all spanning-tree path cost calculations and ultimately leads to the assignment of the different port roles used to prevent loops from occurring.
A root bridge election is triggered after a switch has finished booting up, or when a path failure has been detected on a network. Initially, all switch ports are configured for the blocking state, which by default lasts 20 seconds. This is done to prevent a loop from occurring before STP has had time to calculate the best root paths and configure all switch ports to their specific roles. While the switch ports are in a blocking state, they are still able to send and receive BPDU frames so that the spanning-tree root election can proceed. Spanning tree supports a maximum network diameter of seven switch hops from end to end. This allows the entire root bridge election process to occur within 14 seconds, which is less than the time the switch ports spend in the blocking state.
Immediately after the switches have finished booting up, they start sending BPDU frames advertising their BID in an attempt to become the root bridge. Initially, all switches in the network assume that they are the root bridge for the broadcast domain. The flood of BPDU frames on the network have the root ID field matching the BID field, indicating that each switch considers itself the root bridge. These BPDU frames are sent every 2 seconds based on the default hello timer value.
As each switch receives the BPDU frames from its neighboring switches, they compare the root ID from the received BPDU frame with the root ID configured locally. If the root ID from the received BPDU frame is lower than the root ID it currently has, the root ID field is updated indicating the new best candidate for the root bridge role.
After the root ID field is updated on a switch, the switch then incorporates the new root ID in all future BPDU frame transmissions. This ensures that the lowest root ID is always conveyed to all other adjacent switches in the network. The root bridge election ends once the lowest bridge ID populates the root ID field of all switches in the broadcast domain.
Even though the root bridge election process has completed, the switches continue to forward their BPDU frames advertising the root ID of the root bridge every 2 seconds. Each switch is configured with a max age timer that determines how long a switch retains the current BPDU configuration in the event it stops receiving updates from its neighboring switches. By default, the max age timer is set to 20 seconds. Therefore, if a switch fails to receive 10 consecutive BPDU frames from one of its neighbors, the switch assumes that a logical path in the spanning tree has failed and that the BPDU information is no longer valid. This triggers another spanning-tree root bridge election.
When the root bridge election is completed, you can verify the identity of the root bridge using the show spanning-tree privileged EXEC mode command
In the topology example, switch S1 has the lowest priority value of the three switches, so we can assume it will become the root bridge.
Step 2. Elect Root Ports
Now that the root bridge has been determined, the switches start configuring the port roles for each of their switch ports. The first port role that needs to be determined is the root port role.
Every switch in a spanning-tree topology, except for the root bridge, has a single root port defined. The root port is the switch port with the lowest path cost to the root bridge. Normally path cost alone determines which switch port becomes the root port. However, additional port characteristics determine the root port when two or more ports on the same switch have the same path cost to the root. This can happen when redundant links are used to uplink one switch to another switch when an EtherChannel configuration is not used.
Switch ports with equivalent path costs to the root use the configurable port priority value. They use the port ID to break a tie. When a switch chooses one equal path cost port as a root port over another, the losing port is configured as the non-designated to avoid a loop.
The process of determining which port becomes a root port happens during the root bridge election BPDU exchange. Path costs are updated immediately when BPDU frames arrive indicating a new root ID or redundant path. At the time the path cost is updated, the switch enters decision mode to determine if port configurations need to be updated. The port role decisions do not wait until all switches settle on which switch is going to be the final root bridge. As a result, the port role for a given switch port may change multiple times during convergence, until it finally settles on its final port role after the root ID changes for the last time.
When the root bridge election has completed, you can verify the configuration of the root ports using the show spanning-tree privileged EXEC mode command.
In the topology example, switch S1 has been identified as the root bridge. The switch S2 F0/1 port and switch S3 F0/1 port are the two closest ports to the root bridge and, therefore, should be configured as root ports. You can confirm the port configuration using the show spanning-tree privileged EXEC mode command.
Step 3. Electing Designated Ports and Non-Designated Ports
After a switch determines which of its ports is the root port, the remaining ports must be configured as either a designated port (DP) or a non-designated port (non-DP) to finish creating the logical loop-free spanning tree.
Each segment in a switched network can have only one designated port. When two non-root port switch ports are connected on the same LAN segment, a competition for port roles occurs. The two switches exchange BPDU frames to sort out which switch port is designated and which one is non-designated.
Generally, when a switch port is configured as a designated port, it is based on the BID. However, keep in mind that the first priority is the lowest path cost to the root bridge and that only if the port costs are equal, is the BID of the sender.
When two switches exchange their BPDU frames, they examine the sending BID of the received BPDU frame to see if it is lower than its own. The switch with the lower BID wins the competition and its port is configured in the designated role. The losing switch configures its switch port to be non-designated and, therefore, in the blocking state to prevent the loop from occurring.
The process of determining the port roles happens concurrently with the root bridge election and root port designation. As a result, the designated and non-designated roles may change multiple times during the convergence process until the final root bridge has been determined. The entire process of electing the root bridge, determining the root ports, and determining the designated and non-designated ports happens within the 20-second blocking port state. This convergence time is based on the 2-second hello timer for BPDU frame transmission and the seven-switch diameter supported by STP. The max age delay of 20 seconds provides enough time for the seven-switch diameter with the 2-second hello timer between BPDU frame transmissions.
Verify DP and Non-DP
After the root ports have been assigned, the switches determine which remaining ports are configured as designated and non-designated ports. You can verify the configuration of the designated and non-designated ports using the show spanning-tree privileged EXEC mode command.
STP Topology Change
A switch considers it has detected a topology change either when a port that was forwarding is going down (blocking for instance) or when a port transitions to forwarding and the switch has a designated port. When a change is detected, the switch notifies the root bridge of the spanning tree. The root bridge then broadcasts the information into the whole network.
In normal STP operation, a switch keeps receiving configuration BPDU frames from the root bridge on its root port. However, it never sends out a BPDU toward the root bridge. To achieve that, a special BPDU called the topology change notification (TCN) BPDU was introduced. When a switch needs to signal a topology change, it starts to send TCNs on its root port. The TCN is a very simple BPDU that contains no information and is sent out at the hello time interval. The receiving switch is called the designated bridge and it acknowledges the TCN by immediately sending back a normal BPDU with the topology change acknowledgement (TCA) bit set.
For example, in the figure switch S2 experiences a topology change. It sends a TCN to its designated bridge, which in this case is switch D1. Switch D1 receives the TCN, acknowledges it back to switch S2 with a TCA. Switch D1 generates a TCN, and forwards it to its designated bridge, which in this case is the root bridge.
Broadcast Notification
Once the root bridge is aware that there has been a topology change event in the network, it starts to send out its configuration BPDUs with the topology change (TC) bit set. These BPDUs are relayed by every switch in the network with this bit set. As a result, all switches become aware of the topology change and can reduce their aging time to forward delay. Switches receive topology change BPDUs on both forwarding and blocking ports.
The TC bit is set by the root for a period of max age + forward delay seconds, which is 20+15=35 seconds by default.
Cisco and STP Variants
There are many types or variants of STP. Some of these variants are Cisco proprietary and others are IEEE standards.
Per-VLAN spanning tree protocol (PVST) - Maintains a spanning-tree instance for each VLAN configured in the network. It uses the Cisco proprietary ISL trunking protocol that allows a VLAN trunk to be forwarding for some VLANs while blocking for other VLANs. Because PVST treats each VLAN as a separate network, it can load balance traffic at Layer 2 by forwarding some VLANs on one trunk and other VLANs on another trunk without causing a loop.
Per-VLAN spanning tree protocol plus (PVST+) - Cisco developed PVST+ to provide support for IEEE 802.1Q trunking. PVST+ provides the same functionality as PVST, including the Cisco proprietary STP extensions. PVST+ is not supported on non-Cisco devices. PVST+ includes the PortFast enhancement called BPDU guard, and root guard.
Rapid per-VLAN spanning tree protocol (rapid PVST+) - Based on the IEEE 802.1w standard and has a faster convergence than STP (standard 802.1D). Rapid PVST+ includes Cisco-proprietary extensions such as BackboneFast, UplinkFast, and PortFast.
Rapid spanning tree protocol (RSTP) - It provides faster spanning-tree convergence after a topology change. RSTP implements the Cisco-proprietary STP extensions, BackboneFast, UplinkFast, and PortFast, into the public standard.
Multiple STP (MSTP) - Enables multiple VLANs to be mapped to the same spanning-tree instance, reducing the number of instances needed to support a large number of VLANs. MSTP was inspired by the Cisco-proprietary Multiple Instances STP (MISTP) and is an evolution of STP and RSTP. MSTP provides for multiple forwarding paths for data traffic and enables load balancing.
PVST+
Cisco developed PVST+ so that a network can run an STP instance for each VLAN in the network. With PVST+, more than one trunk can block for a VLAN and load sharing can be implemented. However, implementing PVST+ means that all switches in the network are engaged in converging the network, and the switch ports have to accommodate the additional bandwidth used for each PVST+ instance to send its own BPDUs.
In a Cisco PVST+ environment, you can tune the spanning-tree parameters so that half of the VLANs forward on each uplink trunk. In the figure, port F0/3 on switch S2 is the forwarding port for VLAN 20, and F0/2 on switch S2 is the forwarding port for VLAN 10. This is accomplished by configuring one switch to be elected the root bridge for half of the total number of VLANs in the network, and a second switch to be elected the root bridge for the other half of the VLANs. In the figure, switch S3 is the root bridge for VLAN 20, and switch S1 is the root bridge for VLAN 10. Creating different STP root switches per VLAN creates a more redundant network.
PVST+ Bridge ID
As you recall, in the original 802.1D standard, an 8-byte BID is composed of a 2-byte bridge priority and a 6-byte MAC address of the switch. There was no need to identify a VLAN because there was only one spanning tree in a network. PVST+ requires that a separate instance of spanning tree run for each VLAN. To support PVST+, the 8-byte BID field is modified to carry a VLAN ID (VID).
The following provides more details on the PVST+ fields:
- Bridge priority - A 4-bit field carries the bridge priority. Because of the limited bit count, the priority is conveyed in discrete values in increments of 4096 rather than discreet values in increments of 1, as they would be if the full 16-bit field was available. The default priority, in accordance with IEEE 802.1D, is 32,768, which is the midrange value.
- Extended system ID - A 12-bit field carrying the VID for PVST+.
- MAC address - A 6-byte field with the MAC address of a single switch.
The MAC address is what makes a BID unique. When the priority and extended system ID are prepended to the switch MAC address, each VLAN on the switch can be represented by a unique BID.
Caution: If no priority has been configured, every switch has the same default priority, and the election of the root bridge for each VLAN is based on the MAC address. Therefore, to ensure that you get the root bridge you want, it is advisable to assign a lower priority value to the switch that should serve as the root bridge.
Configure PVST+
The topology shows three switches with 802.1Q trunks connecting them. There are two VLANs, 10 and 20, which are being trunked across these links. This network has not been configured for spanning tree. The goal is to configure S3 as the root bridge for VLAN 20 and S1 as the root bridge for VLAN 10. Port F0/3 on S2 is the forwarding port for VLAN 20 and the blocking port for VLAN 10. Port F0/2 on S2 is the forwarding port for VLAN 10 and the blocking port for VLAN 20.
Configure the Primary Root Bridges
The goal is to configure switch S3 as the primary root bridge for VLAN 20 and configure switch S1 as the primary root bridge for VLAN 10. To configure a switch to become the root bridge for a specified VLAN, use the spanning-tree vlan vlan-ID root primary global configuration mode command.
Configure the Secondary Root Bridges
A secondary root is a switch that may become the root bridge for a VLAN if the primary root bridge fails. To configure a switch as the secondary root bridge, use the spanning-tree vlan vlan-ID root secondary global configuration mode command. Assuming the other bridges in the VLAN retain their default STP priority, this switch becomes the root bridge if the primary root bridge fails. This command can be executed on more than one switch to configure multiple backup root bridges.
PVST+ Switch Priority
You can set the switch priority for the specified spanning-tree instance. This setting affects the likelihood that this switch is selected as the root switch. A lower value increases the probability that the switch is selected. The range is 0 to 61440 in increments of 4096. For example, a valid priority value is 4096x2 = 8192. All other values are rejected.
RSTP
RSTP (IEEE 802.1w) is an evolution of the 802.1D standard. In the figure, a network shows an example of RSTP. Switch S1 is the root bridge with two designated ports in a forwarding state. RSTP supports a new port type. Port F0/3 on switch S2 is an alternate port in discarding state. Notice that there are no blocking ports. RSTP does not have a blocking port state. RSTP defines port states as discarding, learning, or forwarding.
RSTP can achieve much faster convergence in a properly configured network, sometimes in as little as a few hundred milliseconds. RSTP redefines the type of ports and their state. If a port is configured to be an alternate or a backup port it can immediately change to a forwarding state without waiting for the network to converge
RSTP BPDU
RSTP (802.1w) uses type 2, version 2 BPDUs, so an RSTP bridge can communicate 802.1D on any shared link or with any switch running 802.1D. RSTP sends BPDUs and populates the flag byte in a slightly different manner than in 802.1D:
- Protocol information can be immediately aged on a port if hellos are not received for three consecutive hello times, 6 seconds by default, or if the max age timer expires.
- Because BPDUs are used as a keepalive mechanism, three consecutively missed BPDUs indicate lost connectivity between a bridge and its neighboring root or designated bridge. The fast aging of the information allows failures to be detected quickly.
Il Rapid STP (802.1w) ha la stessa funzione di 802.1d ma lo fa più velocemente. La migliore velocità è ottenuta dal fatto che le porte possono passare subito da blocking (discarding) a forwarding.
Note: Like STP, an RSTP bridge sends a BPDU with its current information every hello time period (2 seconds by default), even if the RSTP bridge does not receive any BPDUs from the root bridge.
Edge Ports
An RSTP edge port is a switch port that is never intended to be connected to another switch device. It immediately transitions to the forwarding state when enabled.
The edge port concept is well known to Cisco spanning-tree users, because it corresponds to the PortFast feature in which all ports directly connected to end stations anticipate that no switch device is connected to them. The PortFast ports immediately transition to the STP forwarding state, thereby skipping the time-consuming listening and learning stages. Neither edge ports nor PortFast-enabled ports generate topology changes when the port transitions to a disabled or enabled status.
Unlike PortFast, an RSTP edge port that receives a BPDU loses its edge port status immediately and becomes a normal spanning-tree port.
The Cisco RSTP implementation maintains the PortFast keyword using the spanning-tree portfast command for edge port configuration. Configuring an edge port to be attached to another switch can have negative implications for RSTP when it is in sync state because a temporary loop can result, possibly delaying the convergence of RSTP due to BPDU contention with loop traffic.
RSTP Port States
RSTP provides rapid convergence following a failure or during re-establishment of a switch, switch port, or link. An RSTP topology change causes a transition in the appropriate switch ports to the forwarding state through either explicit handshakes or a proposal and agreement process and synchronization.
With RSTP, the role of a port is separated from the state of a port. For example, a designated port could be in the discarding state temporarily, even though its final state is to be forwarding. The figure shows the three possible RSTP port states: discarding, learning, and forwarding.
In IEEE 802.1D STP, when a port has been selected by spanning tree to become a designated port, it must wait two times the forward delay before transitioning the port to the forwarding state. RSTP significantly speeds up the recalculation process after a topology change, because it converges on a link-by-link basis and does not rely on timers expiring before ports can transition. Rapid transition to the forwarding state can only be achieved on edge ports and point-to-point links. In RSTP, this condition corresponds to a designated port in the discarding state.
Configuring Rapid-PVST+
The figure shows the Cisco IOS command syntax needed to configure rapid-PVST+ on a Cisco switch:
Note: If you connect a port configured with the spanning-tree link-type point-to-point command to a remote port through a point-to-point link and the local port becomes a designated port, the switch negotiates with the remote port and rapidly changes the local port to the forwarding state.
Note: When a port is configured with the clear spanning-tree detected-protocols command and that port is connected to a port on a legacy IEEE 802.1D switch, the Cisco IOS software restarts the protocol migration process on the entire switch
Final Points
Troubleshoot STP Operation
An issue that is not well known relates to the diameter of the switched network. The conservative default values for the STP timers impose a maximum network diameter of seven. In the figure this design creates a network diameter of eight. The maximum network diameter restricts how far away swtiches in the network can be from each other. In this case, two distinct switches cannot be more than seven hops away. Part of this restriction comes from the age field that BPDUs carry.
When a BPDU propagates from the root bridge toward the leaves of the tree, the age field increments each time the BPDU goes though a switch. Eventually, the switch discards the BPDU when the age field goes beyond maximum age. If the root is too far away from some switches of the network, BPDUs will be dropped. This issue affects convergence of the spanning tree.
Take special care if you plan to change STP timers from the default value. There is danger if you try to get faster convergence in this way. An STP timer change has an impact on the diameter of the network and the stability of the STP. You can change the switch priority to select the root bridge, and change the port cost or priority parameter to control redundancy and load balancing.




























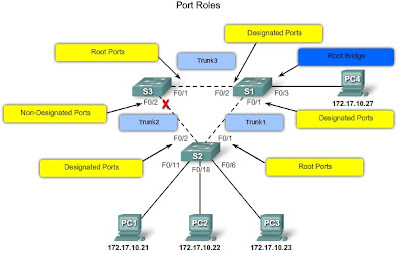

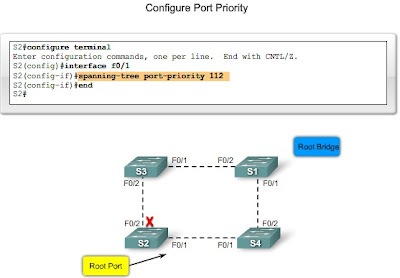































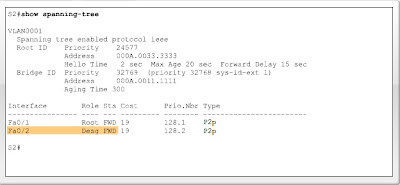























Nessun commento:
Posta un commento