One of the most common types of WAN connection is the point-to-point connection. Point-to-point connections are used to connect LANs to service provider WANs, and to connect LAN segments within an Enterprise network. A LAN-to-WAN point-to-point connection is also referred to as a serial connection or leased-line connection, because the lines are leased from a carrier (usually a telephone company) and are dedicated for use by the company leasing the lines.
Parallel or Serial cable?
Serial links can be clocked considerably faster than parallel links, and they achieve a higher data rate, because of two factors that affect parallel communications: clock skew and crosstalk interference.
TDM
TDM divides the bandwidth of a single link into separate channels or time slots. TDM transmits two or more channels over the same link by allocating a different time interval (time slot) for the transmission of each channel. In effect, the channels take turns using the link.
TDM is a Physical layer concept. It has no regard for the nature of the information that is being multiplexed onto the output channel. TDM is independent of the Layer 2 protocol that has been used by the input channels.
This is the principle used in synchronous TDM when sending data over a link. TDM increases the capacity of the transmission link by slicing time into smaller intervals so that the link carries the bits from multiple input sources, effectively increasing the number of bits transmitted per second. With TDM, the transmitter and the receiver both know exactly which signal is being sent.
Statistical Time Division Multiplexing - STDM uses a variable time slot length allowing channels to compete for any free slot space. It employs a buffer memory that temporarily stores the data during periods of peak traffic. STDM does not waste high-speed line time with inactive channels using this scheme. STDM requires each transmission to carry identification information (a channel identifier).
An example of a technology that uses synchronous TDM is ISDN. ISDN basic rate (BRI) has three channels consisting of two 64 kb/s B-channels (B1 and B2), and a 16 kb/s D-channel. On a larger scale, the telecommunications industry uses the SONET or SDH standard for optical transport of TDM data. SONET and SDH, used elsewhere, are two closely related standards that specify interface parameters, rates, framing formats, multiplexing methods, and management for synchronous TDM over fiber.
The original unit used in multiplexing telephone calls is 64 kb/s, which represents one phone call. It is referred to as a DS-0 or DS0 (digital signal level zero).
Demarcation Point
telephone companies owned the local loop, including the wiring and equipment on the premises of the customers. Deregulation forced telephone companies to unbundle their local loop infrastructure to allow other suppliers to provide equipment and services. This led to a need to delineate which part of the network the telephone company owned and which part the customer owned. This point of delineation is the demarcation point, or demarc. The demarcation point marks the point where your network interfaces with the network owned by another organization. In telephone terminology, this is the interface between customer-premises equipment (CPE) and network service provider equipment. The demarcation point is the point in the network where the responsibility of the service provider ends.
DTE and DCE
From the point of view of connecting to the WAN, a serial connection has a DTE device at one end of the connection and a DCE device at the other end. The connection between the two DCE devices is the WAN service provider transmission network.
- The CPE, which is generally a router, is the DTE. The DTE could also be a terminal, computer, printer, or fax machine if they connect directly to the service provider network.
- The DCE, commonly a modem or CSU/DSU, is the device used to convert the user data from the DTE into a form acceptable to the WAN service provider transmission link. This signal is received at the remote DCE, which decodes the signal back into a sequence of bits. The remote DCE then signals this sequence to the remote DTE.
A null modem is a communication method to directly connect two DTEs, such as a computer, terminal, or printer, using a RS-232 serial cable. With a null modem connection, the transmit (Tx) and receive (Rx) lines are crosslinked. When using a null modem, keep in mind that synchronous connections require a clock signal. An external device can generate the signal, or one of the DTEs can generate the clock signal. When a DTE and DCE are connected, the serial port on a router is the DTE end of the connection by default, and the clock signal is typically provided by a CSU/DSU or similar DCE device.
However, when using a null modem cable in a router-to-router connection, one of the serial interfaces must be configured as the DCE end to provide the clock signal for the connection.
WAN Encapsulation
The more common WAN protocols are:
- HDLC - The default encapsulation type on point-to-point connections, dedicated links, and circuit-switched connections when the link uses two Cisco devices. HDLC is now the basis for synchronous PPP used by many servers to connect to a WAN, most commonly the Internet.
- PPP - Provides router-to-router and host-to-network connections over synchronous and asynchronous circuits. PPP works with several Network layer protocols, such as IP and IPX. PPP also has built-in security mechanisms such as PAP and CHAP
- Serial Line Internet Protocol (SLIP) - A standard protocol for point-to-point serial connections using TCP/IP
- X.25/Link Access Procedure, Balanced (LAPB) - X.25 specifies LAPB, a Data Link layer protocol. X.25 is a predecessor to Frame Relay.
- Frame Relay - Frame Relay is a next generation protocol after X.25. Frame Relay eliminates some of the time-consuming processes (such as error correction and flow control) employed in X.25.
- ATM - The international standard for cell relay in which devices send multiple service types (such as voice, video, or data) in fixed-length (53-byte) cells. Fixed-length cells allow processing to occur in hardware, thereby reducing transit delays.
HDLC
HDLC is a synchronous Data Link layer bit-oriented protocol developed by the International Organization for Standardization (ISO). HDLC was developed from the Synchronous Data Link Control (SDLC) standard. HDLC provides both connection-oriented and connectionless service.
HDLC uses synchronous serial transmission to provide error-free communication between two points. HDLC defines a Layer 2 framing structure that allows for flow control and error control through the use of acknowledgments. Each frame has the same format, whether it is a data frame or a control frame. HDLC uses a frame delimiter, or flag, to mark the beginning and the end of each frame.
Cisco has developed an extension to the HDLC protocol to solve the inability to provide multiprotocol support. Although Cisco HDLC (also referred to as cHDLC) is proprietary, Cisco has allowed many other network equipment vendors to implement it. Cisco HDLC frames contain a field for identifying the network protocol being encapsulated.
HDLC defines three types of frames, each with a different control field format.
Flag - The flag field initiates and terminates error checking. The frame always starts and ends with an 8-bit flag field. The bit pattern is 01111110. Because there is a likelihood that this pattern occurs in the actual data, the sending HDLC system always inserts a 0 bit after every five 1s in the data field, so in practice the flag sequence can only occur at the frame ends. The receiving system strips out the inserted bits. When frames are transmitted consecutively, the end flag of the first frame is used as the start flag of the next frame.
Address - The address field contains the HDLC address of the secondary station. This address can contain a specific address, a group address, or a broadcast address.
Control - The control field uses three different formats, depending on the type of HDLC frame used:
- Information (I) frame: I-frames carry upper layer information and some control information. This frame sends and receives sequence numbers, and the poll final (P/F) bit performs flow and error control. The send sequence number refers to the number of the frame to be sent next. The receive sequence number provides the number of the frame to be received next. Both sender and receiver maintain send and receive sequence numbers.
- Supervisory (S) frame: S-frames provide control information. An S-frame can request and suspend transmission, report on status, and acknowledge receipt of I-frames.
- Unnumbered (U) frame: U-frames support control purposes and are not sequenced. A U-frame can be used to initialize secondaries
Protocol - (only used in Cisco HDLC) This field specifies the protocol type.
Data - The data field contains a path information unit (PIU) or exchange identification (XID) information.
Frame check sequence (FCS) - The FCS precedes the ending flag delimiter and is usually a cyclic redundancy check (CRC) calculation remainder. The CRC calculation is redone in the receiver. If the result differs from the value in the original frame, an error is assumed.
Configuring HDLC Encapsulation
Cisco HDLC is the default encapsulation method used by Cisco devices on synchronous serial lines.
You use Cisco HDLC as a point-to-point protocol on leased lines between two Cisco devices. If you are connecting to a non-Cisco device, use synchronous PPP.
If the default encapsulation method has been changed, use the encapsulation hdlc command in privileged mode to re-enable HDLC.
The output of the show interfaces serial command displays information specific to serial interfaces. When HDLC is configured, "Encapsulation HDLC" should be reflected in the output
The show controllers command is another important diagnostic tool when troubleshooting serial lines. The output indicates the state of the interface channels and whether a cable is attached to the interface.
PPP
Cisco HDLC can only work with other Cisco devices. However, when you need to connect to a non-Cisco router, you should use PPP encapsulation. There are many advantages to using PPP:
- The link quality management feature monitors the quality of the link. If too many errors are detected, PPP takes the link down.
- PPP supports PAP and CHAP authentication.
PPP contains three main components:
- HDLC protocol for encapsulating datagrams over point-to-point links.
- Extensible Link Control Protocol (LCP) to establish, configure, and test the data link connection.
- Family of Network Control Protocols (NCPs) for establishing and configuring different Network layer protocols
PPP Architecture
The figure maps the layered architecture of PPP against the Open System Interconnection (OSI) model. PPP and OSI share the same Physical layer, but PPP distributes the functions of LCP and NCP differently.
At the Physical layer, you can configure PPP on a range of interfaces, including:
- Asynchronous serial
- Synchronous serial
- HSSI
- ISDN
PPP operates across any DTE/DCE interface (RS-232-C, RS-422, RS-423, or V.35). The only absolute requirement imposed by PPP is a duplex circuit, either dedicated or switched, that can operate in either an asynchronous or synchronous bit-serial mode, transparent to PPP link layer frames. PPP does not impose any restrictions regarding transmission rate other than those imposed by the particular DTE/DCE interface in use.
Most of the work done by PPP is at the data link and Network layers by the LCP and NCPs. The LCP sets up the PPP connection and its parameters, the NCPs handle higher layer protocol configurations, and the LCP terminates the PPP connection.
The LCP is the real working part of PPP. The LCP sits on top of the Physical layer and has a role in establishing, configuring, and testing the data-link connection. The LCP establishes the point-to-point link. The LCP also negotiates and sets up control options on the WAN data link, which are handled by the NCPs.
The LCP provides automatic configuration of the interfaces at each end, including:
- Handling varying limits on packet size
- Detecting common misconfiguration errors
- Terminating the link
- Determining when a link is functioning properly or when it is failing
PPP also uses the LCP to agree automatically on encapsulation formats (authentication, compression, error detection) as soon as the link is established.
PPP permits multiple Network layer protocols to operate on the same communications link. For every Network layer protocol used, PPP uses a separate NCP. For example, IP uses the IP Control Protocol (IPCP), and IPX uses the Novell IPX Control Protocol (IPXCP). NCPs include functional fields containing standardized codes to indicate the Network layer protocol that PPP encapsulates.
The LCP can negotiate modifications to the standard PPP frame structure.
Establishing a PPP Session
The figure shows the three phases of establishing a PPP session:
Phase 1: Link establishment and configuration negotiation - Before PPP exchanges any Network layer datagrams (for example, IP), the LCP must first open the connection and negotiate configuration options. This phase is complete when the receiving router sends a configuration-acknowledgment frame back to the router initiating the connection.
Phase 2: Link quality determination (optional) - The LCP tests the link to determine whether the link quality is sufficient to bring up Network layer protocols. The LCP can delay transmission of Network layer protocol information until this phase is complete.
Phase 3: Network layer protocol configuration negotiation - After the LCP has finished the link quality determination phase, the appropriate NCP can separately configure the Network layer protocols, and bring them up and take them down at any time. If the LCP closes the link, it informs the Network layer protocols so that they can take appropriate action.
PPP can terminate the link at any time. This might happen because of the loss of the carrier, authentication failure, link quality failure, the expiration of an idle-period timer, or the administrative closing of the link. The LCP closes the link by exchanging Terminate packets.
NCP Process
After the link has been initiated, the LCP passes control to the appropriate NCP. PPP can carry data from many types of Network layer protocols. It can also carry two or more Layer 3 protocols simultaneously. After the LCP has configured and authenticated the basic link, the appropriate NCP is invoked to complete the specific configuration of the Network layer protocol being used. When the NCP has successfully configured the Network layer protocol, the network protocol is in the open state on the established LCP link. At this point, PPP can carry the corresponding Network layer protocol packets.
PPP Configuration Options
PPP may include the following LCP options:
- Authentication - Peer routers exchange authentication messages. Two authentication choices are Password Authentication Protocol (PAP) and Challenge Handshake Authentication Protocol (CHAP).
- Compression - Increases the effective throughput on PPP connections by reducing the amount of data in the frame that must travel across the link. The protocol decompresses the frame at its destination. Two compression protocols available in Cisco routers are Stacker and Predictor.
- Error detection - Identifies fault conditions. The Quality and Magic Number options help ensure a reliable, loop-free data link. The Magic Number field helps in detecting links that are in a looped-back condition. Until the Magic-Number Configuration Option has been successfully negotiated, the Magic-Number must be transmitted as zero. Magic numbers are generated randomly at each end of the connection.
- Multilink - Cisco IOS Release 11.1 and later supports multilink PPP. This alternative provides load balancing over the router interfaces that PPP uses
- PPP Callback - To enhance security, Cisco IOS Release 11.1 and later offers callback over PPP
To set PPP as the encapsulation method used by a serial or ISDN interface, use the encapsulation ppp interface configuration command.
The following example enables PPP encapsulation on serial interface 0/0/0:
R3#configure terminal
R3(config)#interface serial 0/0/0
R3(config-if)#encapsulation ppp
The encapsulation ppp command has no arguments, however, you must first configure the router with an IP routing protocol to use PPP encapsulation. You should recall that if you do not configure PPP on a Cisco router, the default encapsulation for serial interfaces is HLDC.
You can configure point-to-point software compression on serial interfaces after you have enabled PPP encapsulation.
To configure compression over PPP, enter the following commands:
R3(config)#interface serial 0/0/0
R3(config-if)#encapsulation ppp
R3(config-if)#compress [predictor | stac]
The command ppp quality percentage ensures that the link meets the quality requirement you set; otherwise, the link closes down.
The percentages are calculated for both incoming and outgoing directions. If the link quality percentage is not maintained, the link is deemed to be of poor quality and is taken down
R3(config)#interface serial 0/0/0
R3(config-if)#encapsulation ppp
R3(config-if)#ppp quality 80
Use the no ppp quality command to disable LQM.
MPPP allows packets to be fragmented and sends these fragments simultaneously over multiple point-to-point links to the same remote address. The multiple physical links come up in response to a user-defined load threshold. MPPP can measure the load on just inbound traffic, or on just outbound traffic, but not on the combined load of both inbound and outbound traffic.
The following commands perform load balancing across multiple links:
Router(config)#interface serial 0/0/0
Router(config-if)#encapsulation ppp
Router(config-if)#ppp multilink
The multilink command has no arguments. To disable PPP multilink, use the no ppp multilink command.
Use the show interfaces serial command to verify proper configuration of HDLC or PPP encapsulation.
Use the show interfaces serial command to verify proper configuration of HDLC or PPP encapsulation.
A good command to use when troubleshooting serial interface encapsulation is the debug ppp packet command. Output from the debug ppp packet command as seen from the Link Quality Monitor (LQM) side of the connection. This display example depicts packet exchanges under normal PPP operation.
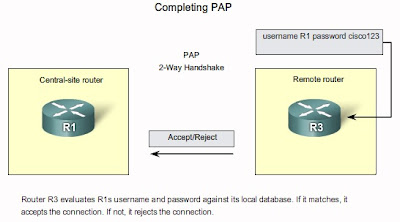
PAP Authentication Protocol
PAP is a very basic two-way process. There is no encryption-the username and password are sent in plain text. If it is accepted, the connection is allowed. CHAP is more secure than PAP. It involves a three-way exchange of a shared secret. The process is described later in this section.
The authentication phase of a PPP session is optional. If used, you can authenticate the peer after the LCP establishes the link and choose the authentication protocol. If it is used, authentication takes place before the Network layer protocol configuration phase begins.
One of the many features of PPP is that it performs Layer 2 authentication in addition to other layers of authentication, encryption, access control, and general security procedures. PAP provides a simple method for a remote node to establish its identity using a two-way handshake. PAP is not interactive. When the ppp authentication pap command is used, the username and password are sent as one LCP data package, rather than the server sending a login prompt and waiting for a response.
PAP is not a strong authentication protocol. Using PAP, you send passwords across the link in clear text and there is no protection from playback or repeated trial-and-error attacks. The remote node is in control of the frequency and timing of the login attempts.
Challenge Handshake Authentication Protocol (CHAP)
Once authentication is established with PAP, it essentially stops working. This leaves the network vulnerable to attack. Unlike PAP, which only authenticates once, CHAP conducts periodic challenges to make sure that the remote node still has a valid password value.
After the PPP link establishment phase is complete, the local router sends a challenge message to the remote node. The remote node responds with a value calculated using a one-way hash function, which is typically Message Digest 5 (MD5) based on the password and challenge message.
The local router checks the response against its own calculation of the expected hash value. If the values match, the initiating node acknowledges the authentication. Otherwise, it immediately terminates the connection.
The ppp authentication Command
To specify the order in which the CHAP or PAP protocols are requested on the interface, use the ppp authentication interface configuration command, as shown in the figure. Use the no form of the command to disable this authentication.
You may enable PAP or CHAP or both. If both methods are enabled, the first method specified is requested during link negotiation. If the peer suggests using the second method or simply refuses the first method, the second method is tried. PAP usernames and passwords are sent as clear-text strings and can be intercepted and reused. CHAP has eliminated most of the known security holes.
Configuring PPP Authentication




























Nessun commento:
Posta un commento